Automated Methodologies for Secure, Trusted Computing Systems
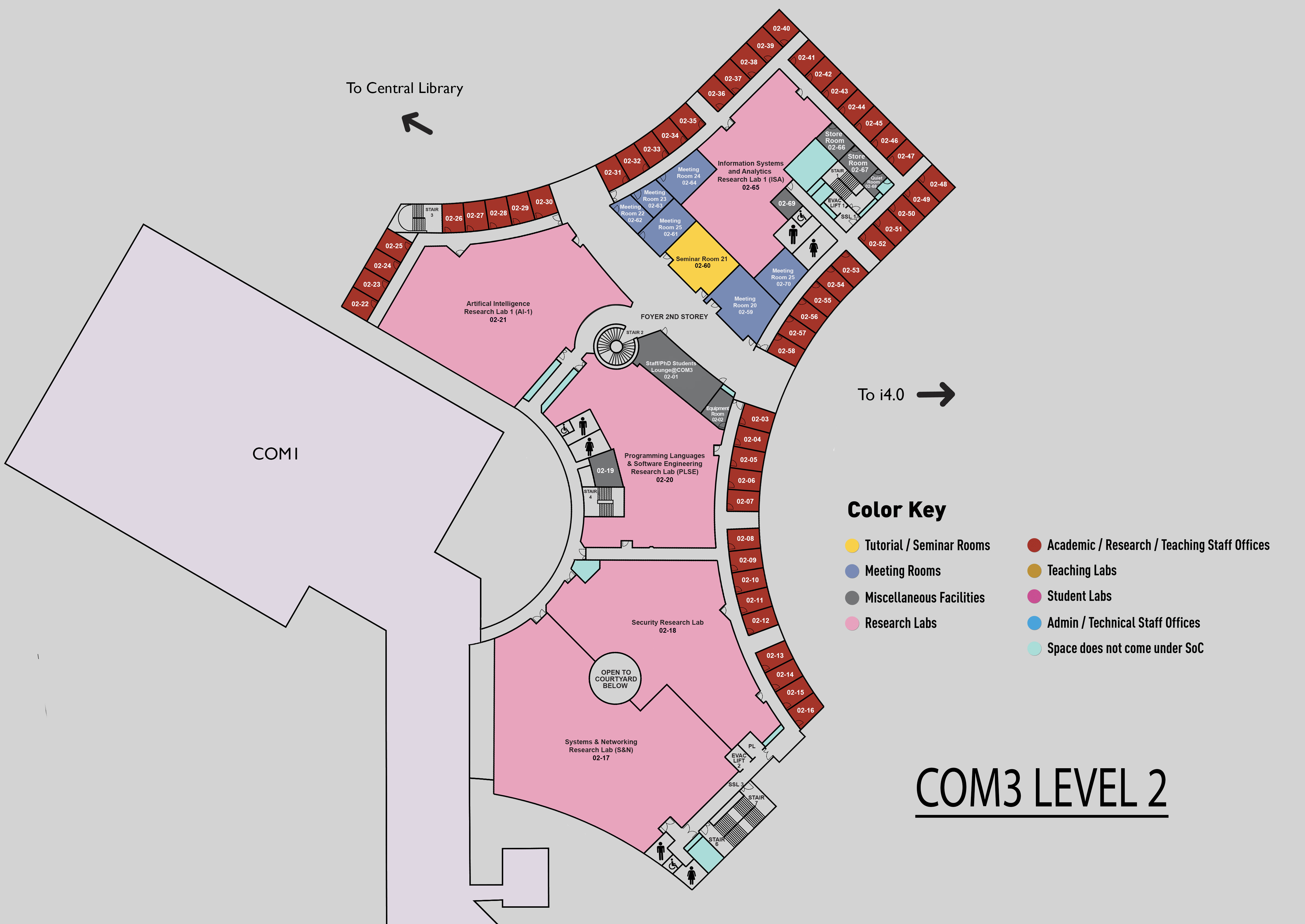
COM3 Level 2
SR21, COM3 02-60
Abstract:
The world is moving toward the Internet-of-Things (IoT) era where computing systems are ubiquitous and can be found in a variety of applications. The growth of computing systems has exponentially increased over the past few decades to support more sophisticated applications. Currently, computing systems have become highly prevalent to the point that computing systems are part of the most aspects of daily lives and in critical sectors including financial, military, industrial and transportation sectors, creating security risks that have to be addressed. Due to this growing reliance on computing systems, hardware security has become a main concern and key dimension that circuit designers have to consider during design time. Methodologies that allow circuits designers to design secure, trusted computing systems are critically needed to ensure that computing systems will not be compromised during deployment.
Fault injection attacks are one of the key threats in the IoT era that aim to directly inject faults to devices. This is due to the proliferation and prevalence of computing systems in this IoT era which allow attackers to gain physical access to these devices to perform fault injection attacks. These attacks are conducted with the goals to compromise confidentiality, integrity, and availability of devices, using a variety of techniques that force devices to operate in an environment that is not expected. Fault injection attacks are relatively more powerful than other software attacks. Also, removing vulnerabilities found after chip fabrication could be difficult and require hardware design changes, which is too late. To protect designs against these attacks, a tool that allows circuit designers to simulate these attacks early during design time and to integrate defenses to the designs are essential.
Semiconductor companies rely on other third-parties to facilitate chip development from purchasing IP blocks to using chip manufacturing services to stay competitive. Relying on third-parties creates large attack surfaces as some of these companies can be untrusted and intentionally add undesirable components called hardware Trojans. Hardware Trojans are malicious components that are covertly added to chips to prevent chips from operating as expected. They are designed to be stealthy to ensure that they cannot be easily detected, can circumvent detection methodologies, and will be activated during deployment at critical times. There are hardware Trojan detection methodologies that could be deployed in different stages of the design flow. However, they do not guarantee that all hardware Trojans are detected. Run-time hardware Trojan detection is essential as the last layer of defense to ensure that hardware Trojans can be detected during deployment.
This talk focuses on these two major attack classes in hardware security. Fault injection attacks and their applications will be presented. Then, I will talk about the Laser Attack Benchmark Suite (LABS) which is a tool that allows circuit designers to evaluate their designs against laser fault injection attacks and to automatically integrate a hardware-based redundancy defense to their designs. A walkthrough demonstrating how LABS is used to simulate laser fault injection attacks and protect designs against these attacks will be demonstrated. After that, I will talk about challenges of detecting hardware Trojans and propose an analytical modeling-based hardware Trojan detection methodology which provides high detection accuracy while occurring negligible power overhead at 0.005%. Then, an automated, flexible methodology that generates hardware Trojan countermeasures for network-on-chips will be presented. Finally, a graph processing accelerator which allows for automated hardware Trojan detection will be elaborated.

